~hackernoon | Bookmarks (2049)
-
IPinfo Launches IPinfo Lite: Unlimited Country-Level Geolocation API & Database Download
IPinfo has launched IPinfo Lite, a free, unlimited-use IP geolocation and ASN data product with daily...
-
The ESPRIT Algorithm and Central Limit Error Scaling
The ESPRIT algorithm starts by rearranging the noisy measurements into a Hankel or Toeplitz matrix. In...
-
Optimal Error Scaling of ESPRIT Algorithm Demonstrated
We present a novel analysis proving the ESPRIT algorithm achieves optimal error scaling for spectral estimation
-
BingX Unveils ChainSpot: A CeDeFi Innovation for Simpler and Safer On-Chain Trading
BingX is proud to unveil ChainSpot, a pioneering CeDeFi (Centralized-Decentralized Finance) feature that empowers users to...
-
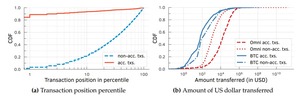
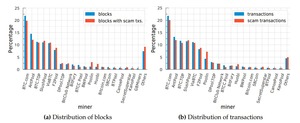
Uncovering Hidden Bias in Blockchain Transaction Ordering
This chapter presents the first empirical evidence of Bitcoin miner deviation from fair transaction norms, examines...
-
Meet YellowLyfe HQ, Sufle, and Green Cross United Kingdom: HackerNoon Startups of The Week
Each week, the HackerNoon team highlights standout Startups from our Startups of The Year database. Every...
-
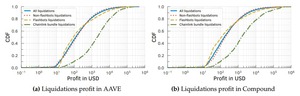
Power Concentration and Voting Dynamics in Compound Governance
Compound’s on‑chain governance is active but heavily centralized: a handful of addresses hold and delegate most...
-
Want Trustworthy AI? Put It on the Blockchain
TLDR: AI is super powerful but often feels like a mysterious "black box," and the tech...
-
Flipster Makes Esports Debut As Official Crypto Exchange Partner Of TALON’s Dota 2 Team
Flipster announces partnership with TALON, one of Asia’s premier competitive gaming organizations. As part of the...
-
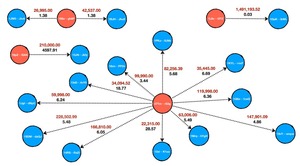
essons from Balancer’s and Alameda Research’s Governance Hacks
Token concentration undermines DeFi governance—Balancer saw a large holder push self‑serving proposals, Alameda Research used its...
-
Deadzone: Rogue Rockets To Steam's Top 10 Global Sellers With 100K+ Players In Week 1
Deadzone: Rogue has officially launched into Early Access on Steam. The game has received praise for...
-
Your Data Called—It Wants To Break Up With Big Tech!
Decentralized AI is a new way to store, process and share data. It lets you control...
-
How Space and Time's Mainnet Launch Could Reshape Data Access in Web3
Space and Time launches its mainnet, introducing ZK-proven data queries for smart contracts. Here's how it...
-
How Token Concentration and Voting Costs Impact Compound Governance
This chapter outlines a methodology using an Ethereum archive node and event logs to analyze Compound...
-
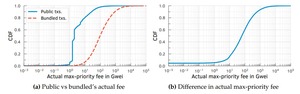
How Flashbots Bundles and Dark‑Fees Break Blockchain Transparency
Flashbots now powers 2% of Ethereum txs in 52% of blocks, bundling public DEX calls or...
-
The Ethical Hacker's Guide to Hacking WiFi with Termux
Learn ethical WiFi hacking with Termux and Wipwn. This guide covers setup, Pixie Dust attacks, WPS...
-
We Wrote a Code Review Guide—Here's What Worked
We created a code review guide to align expectations, improve feedback quality, and make reviews feel...
-
Remotely Control Youtube With This Command-line Approach on Linux
You can control youtube form the command in linux. But it's a little work. This article...
-
The Search Stack That Nearly Broke Us — Until We Did This
Finlight.me moved from Postgres full-text search to OpenSearch. The move was made to support the fast,...
-
Seamlessly Install Magnolia CMS With This Guide
This guide provides a step-by-step process for installing Magnolia CMS version 6.2, covering prerequisites like Java,...
-
How Special Relays Let Some Ethereum Transactions Skip the Public Queue
Contention transparency fails in Ethereum as private relay networks like Flashbots and Taichi let miners receive...
-
How Hacktivists Plan to Combat Misinformation in the Future
Hacktivists are determined to combat misinformation through coordinated strategies, including truth-spreading bots, misinformation literacy, and hacking...
-
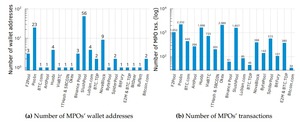
Monero Vs. The Regulators: A Technical Analysis of Privacy Under Scrutiny
Monero stands out as a privacy-focused cryptocurrency that shields transactions from surveillance through innovative technologies like...
-
How We Collected Bitcoin/Ethereum Data and Tested Miner Collusion
We use two large block ranges (Bitcoin 2018–20, Ethereum Sep 2021–Jun 2022), identify public vs. private bundles via...