Better Dev Link
Feed since 23 Mar 2019BetterDev.Link collects links around the web that aims to help you learn something new. The topics aren't tight to any specific programming languages, technologies or frameworks but attempt to include resources that might help you learn a thing or two from them. See: https://betterdev.link/
To subscribe to and get updates from Better Dev Link in your feed stream, sign up, or see the rest of our feeds.
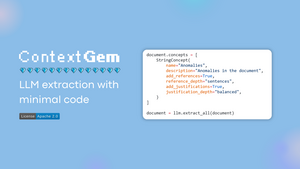
GitHub - shcherbak-ai/contextgem: ContextGem: Effortless LLM extraction from documents
contextgem Effortless LLM extraction from documents

GitHub - microsoft/markitdown: Python tool for converting files and office documents to Markdown.
markitdown Python tool for converting files and office documents to Markdown.
GitHub - neon443/AirAP: airplay to an ios device
AirAP airplay to an ios device, use your iphone as an airplay receiver

GitHub - trimstray/the-book-of-secret-knowledge: A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more.
The Book of Secret Knowledge A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web...
GitHub - dontriskit/awesome-ai-system-prompts: 🧠 Curated collection of system prompts for top AI tools. Perfect for AI agent builders and prompt engineers. Incuding: ChatGPT, Claude, Perplexity, Ma...
Crafting Effective Prompts for Agentic AI Systems: Patterns and Practices Curated collection of system prompts for...

GitHub - mgechev/revive: 🔥 ~6x faster, stricter, configurable, extensible, and beautiful drop-in replacement for golint
revive 🔥 ~6x faster, stricter, configurable, extensible, and beautiful drop-in replacement for golint
GitHub - hapostgres/pg_auto_failover: Postgres extension and service for automated failover and high-availability
pg_auto_failover Postgres extension and service for automated failover and high-availability
GitHub - crystaldba/postgres-mcp: Postgres MCP Pro provides configurable read/write access and performance analysis for you and your AI agents.
postgres-mcp Postgres MCP Pro is an open source Model Context Protocol (MCP) server built to support...

GitHub - koaning/smartfunc: Turn docstrings into LLM-functions
Turn docstrings into LLM-functions

Your data, built your way. Twilio Segment. For data you can depend on.
Your data, built your way. Twilio Segment. For data you can depend on. Customer Data You...
What is Entropy?
What is Entropy? People say many things about entropy: entropy increases with time, entropy is disorder,...

How DCI Movie Delivery and Encryption works
How DCI Movie Delivery and Encryption works The Cinema Industry is using its own standards for...
Talking To Your Mailserver Is Not as Hard as You Think!
Talking To Your Mailserver Is Not as Hard as You Think! Email is very well distributed...
Field Notes From Shipping Real Code With Claude - diwank's space
Field Notes From Shipping Real Code With Claude Think of this post as your field guide...

Building an AI Server on a Budget ($1.3K) | information gain
Building an AI Server on a Budget Instead of renting the GPU we can pay up-front...
X-Ray Defence: Hidden Resource, Sudden Lifeline
X-Ray Defence: Hidden Resource, Sudden Lifeline
Taking out the Trash: Garbage Collection of Object Storage at Massive Scale
Taking out the Trash: Garbage Collection of Object Storage at Massive Scale

A Trip Down Memory Lane: How We Resolved a Memory Leak When pprof Failed Us
A Trip Down Memory Lane: How We Resolved a Memory Leak When pprof Failed Us
TikTok VM Reverse Engineering (webmssdk.js)
TikTok VM Reverse Engineering (webmssdk.js)

goavatar
goavatar This package provides a simple way to generate unique, symmetric identicons based on an input...
GitHub - Stability-AI/stable-virtual-camera: Stable Virtual Camera: Generative View Synthesis with Diffusion Models
stable-virtual-camera Generative View Synthesis with Diffusion Models

30 years of PostgreSQL buffer manager locking design evolution
30 years of PostgreSQL buffer manager locking design evolution An in-depth exploration of the evolution of...

How to Write Blog Posts that Developers Read
How to Write Blog Posts that Developers Read A guide offering practical advice on crafting technical...

Identity Tokens Explained: Best Practices for Better Access Control
Identity Tokens Explained: Best Practices for Better Access Control An overview of identity tokens, detailing their...

Blasting Past Webp
Blasting Past Webp: An analysis of the NSO BLASTPASS iMessage exploit A technical analysis by Google’s...
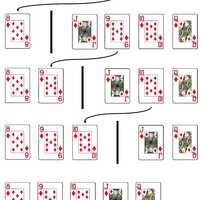
Visual-Focused Algorithms Cheat Sheet
Visual-Focused Algorithms Cheat Sheet A concise reference guide summarizing key algorithms related to visual data processing,...

Train & Weather Tracker with Raspberry Pi & E-Ink
Train & Weather Tracker with Raspberry Pi & E-Ink If you have some old Raspberry Pi...
MySQL transactions per second vs fsyncs per second
MySQL transactions per second vs fsyncs per second An examination of the relationship between MySQL’s transaction...
Laurence Tratt: Better Shell History Search
Better Shell History Search An article discussing techniques to enhance shell history search functionality, including the...
Life Altering Postgresql Patterns
Life Altering PostgreSQL Patterns A discussion on transformative PostgreSQL design patterns, such as using UUID primary...
A Practical Guide to Taming Postgres Isolation Anomalies
A Practical Guide to Taming Postgres Isolation Anomalies A comprehensive guide addressing PostgreSQL’s transaction isolation anomalies,...
Open-sourcing OpenPubkey SSH (OPKSSH): integrating single sign-on with SSH
Cloudflare open-sourcing OpenPubkey SSH (OPKSSH): integrating single sign-on with SSH Single sign-on for SSH is a...
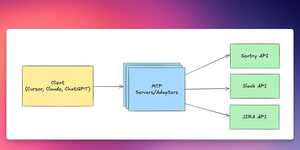
MCP (Model Context Protocol): Simply explained in 5 minutes
MCP (Model Context Protocol): Simply explained in 5 minutes An introduction to the Model Context Protocol...
GitHub - habedi/hann: A fast approximate nearest neighbor search library for Go
hann A fast approximate nearest neighbor search library for Go
GitHub - Kither12/shezem-rs: Audio recognition CLI
shezem-rs A Rust implementation of a fast audio fingerprinting system inspired by Shazam, for audio recognition...
GitHub - pgr0ss/pgledger: A ledger implementation in PostgreSQL
pgledger A ledger implementation in PostgreSQL
GitHub - amd/gaia: Run LLM Agents on Ryzen AI PCs in Minutes
gaia A tool by AMD to run LLM Agents on Ryzen AI PCs in Minutes
GitHub - joanrod/star-vector: StarVector is a foundation model for SVG generation that transforms vectorization into a code generation task. Using a vision-language modeling architecture, StarVecto...
star-vector a foundation model for SVG generation that transforms vectorization into a code generation task. Using...
GitHub - gopasspw/gopass: The slightly more awesome standard unix password manager for teams
gopass The slightly more awesome standard unix password manager for teams
GitHub - lakekeeper/lakekeeper: Lakekeeper is an Apache-Licensed, secure, fast and easy to use Apache Iceberg REST Catalog written in Rust.
lakekeeper an Apache-Licensed, secure, fast and easy to use Apache Iceberg REST Catalog written in Rust....
Zero-knowledge proofs
Zero-Knowledge Proofs An approachable introduction to the magic of zero-knowledge proofs—how they let you prove something...
typespec.io
typespec Define your API once in a simple tsp file, then generate OpenAPI, gRPC, client code,...
pgFormatter
pgFormatter Free Online version of pgFormatter a PostgreSQL SQL syntax beautifier (no line limit here up...
GitHub - xataio/agent: AI agent expert in PostgreSQL
xata agent an open source agent that monitors your database, finds root causes of issues, and...
Intro - Ruby, Ractors, and Lock-Free Data Structures
Ruby Ractors and Lock-Free Data Structures If you’re a Rubyist curious about parallelism, this is for...
BPF or How I Learned to Stop Worrying and Love the Kernel
BPF: Or How I Stopped Worrying and Loved the Kernel BPF is like a superpower for...
A Deep Dive into the Inline Background Overlap Problem – Frontend Masters Blog
A Deep Dive into the Inline Background Overlap Problem Ever tried putting text over an image...
Leaking Passwords (and more!) on macOS | Watch This Space
Leaking Passwords (and more!) on macOS A deep dive into how macOS can unintentionally leak sensitive...
Understanding Solar Energy
Understanding Solar Energy This one’s a bit outside the usual programming realm, but trust me—it’s fascinating....